| Version 21 (modified by , 3 years ago) ( diff ) |
|---|
Security in Aritificial Intelligence
Security in Artificial Intelligence
WINLAB Summer Internship 2023
Advisors: Yingying Chen, Tianfang Zhang, Changming Li, Hong Li
Group Members: Rut Mehta, Jacob Morin, Ethan Lung, Damon Lin
Project Objective
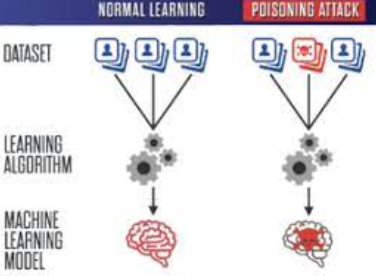
Artificial intelligence techniques have been widely integrated into mobile and IoT devices, enabling various functionalities based on vision (e.g., face recognition, speech recognition, and speaker identification). The extended pipeline of building deep neural networks (DNN) produces new attack surfaces, such as attacks during the data collection, model training, and model update stages. Recent research studies discovered an effective yet stealthy attack, called a backdoor attack, which trains a hidden trigger pattern into the DNNs. The backdoored DNNs will misclassify an input as an adversary-specified label if the trigger pattern appears, behaving normally otherwise, making it difficult to be detected. This project focuses on improving the security behind user authentication through conventional means (e.g., passwords and facial detection) by replacing it with a biometric signature in the form of daily activities. Following this implementation, the project aims to study the vulnerabilities of backdoor attacks on such a system and develop techniques for attack mitigation.
Week 1
Summary
- Established project objectives
- Covered and reviewed background information on topics (adversarial attacks, backdoor attacks, etc.)
- Developed a plan of action for the upcoming weeks
Resources
Week 2
Summary
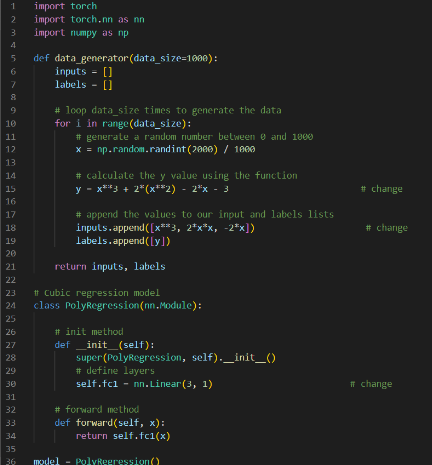
- Familiarized ourselves with PyTorch
- Started researching papers about Smart User Authentication (WiFi-enabled IOT)
- Explored attack mitigation
Resources
https://pytorch.org/tutorials/beginner/basics/intro.html
Week 3
Summary
- Continued learning advanced PyTorch functions for IoT interference data.
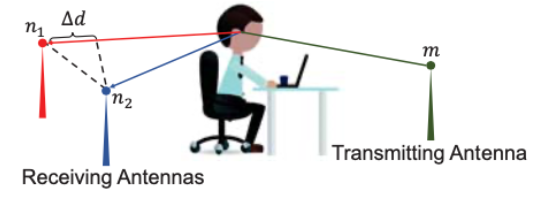
- Set up experiments to collect interference data from mobile devices
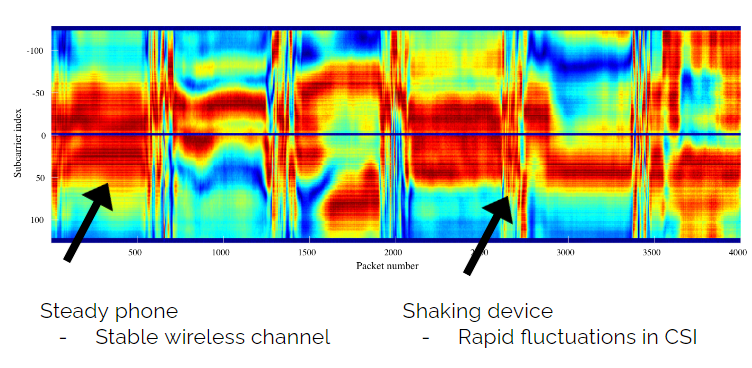
- Examined Channel State Information (CSI) Amplitudes
Resources
http://tns.thss.tsinghua.edu.cn/wst/docs/pre/
Week 4
Summary
- Set up Linux virtual machine through VirtualBox (Ubuntu)
- Familiarized ourselves with Linux Terminal
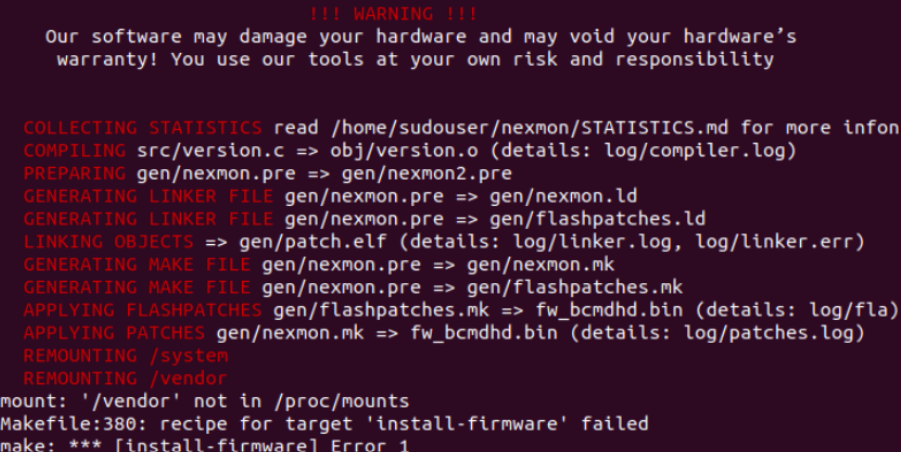
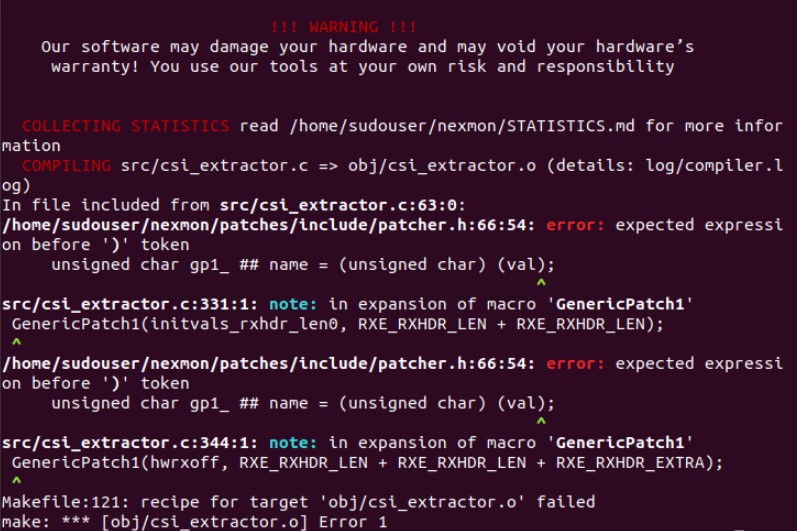
- Installed Nexmon (Channel State Information tool, Extract CSI from phone)
- Used Android Phones (Nexus 5 & Nexus 6) to perform experiments
Resources
https://github.com/seemoo-lab/nexmon_csi#getting-started
Week 5
Summary
- Installed custom ROMs on both the Nexus 5 and Nexus 6
- Resolved Nexus 5 WiFi bug
- Installed suggested Android version for Nexus 6
Week 6
Week 7
Week 8
Week 9
Week 10
Attachments (17)
-
1412.6572.pdf
(1012.1 KB
) - added by 3 years ago.
EXPLAINING AND HARNESSING ADVERSARIAL EXAMPLES
- Screenshot 2023-07-06 110340.png (68.4 KB ) - added by 3 years ago.
- Screenshot 2023-07-06 110736.png (351.7 KB ) - added by 3 years ago.
- {038A11F1-8AFA-4FD5-ACAA-462CE34D7381}.png (60.6 KB ) - added by 3 years ago.
- {5C10995F-B102-434A-B0D0-4469118B9B63}.png (68.3 KB ) - added by 3 years ago.
- {C52B7779-4CD1-40A3-9938-9711E34DFB86}.png (97.7 KB ) - added by 3 years ago.
- {C5E828CF-69BF-4DB6-9960-6A1E754AC68B}.png (65.7 KB ) - added by 3 years ago.
- {30880812-ECF5-4090-B6C4-E00FFA0DF872}.png (54.4 KB ) - added by 3 years ago.
- Screenshot 2023-07-13 100935.png (305.8 KB ) - added by 3 years ago.
- nexus 6 error.jpg (116.9 KB ) - added by 3 years ago.
- csi_test_results.png (84.2 KB ) - added by 3 years ago.
- transmitted_packets.png (18.0 MB ) - added by 3 years ago.
- id_confusion_matrix.png (55.2 KB ) - added by 3 years ago.
- jacob_kick (1).gif (2.2 MB ) - added by 3 years ago.
- 1712.05526.pdf (5.8 MB ) - added by 3 years ago.
- securityai_flowchart2.png (185.3 KB ) - added by 3 years ago.
- securityai_experiment_setup.png (1.6 MB ) - added by 3 years ago.