Effective Password Cracking Using GPU
Table of Contents
- 2015 Winlab Summer Internship
- LTE Unlicensed (LTE-U)
- Introduction
- Objectives
- Theory
- Analyzing Tools
- Experiment 1: Transmit and Receive LTE Signal
- Experiment 2: The Waterfall Plot
- Experiment 3: eNB and UE GUI
- Experiment 4: Varying Bandwidths
- Experiment 5: Working with TDD or FDD
- Experiment 6: TDD with Varying Bandwidths
- Experiment 7: TDD Waterfall Plot
- Poster
- Members
- Materials
- Resources
- LTE Unlicensed (LTE-U)
- Body Sensor Networks
- Dynamic Video Encoding
Introduction
In cryptanalysis and computer security, password cracking is the process of recovering passwords from data that have been stored in or transmitted by a computer system. There are two types of attack: one is Brute-force attack and the other is Dictionary attack. A common approach (brute-force attack) is to try guesses repeatedly for the password and check them against an available cryptographic hash of the password. A dictionary attack is defeating a cipher by trying to determine its decryption key or passphrase by trying hundreds or sometimes millions of likely possibilities. It generates the hash from the dictionary entry and then compares them with the passwords.
A GPU has hundres of cores that can be used to compute mathematical functions in parallel. A CPU usually has 2-8 cores. Although a CPU core is much faster than a GPU core, password hashing is one of the functions that can be done in parallel very easily. This is what gives GPUs a massive edge in cracking passwords. A GPU is excellent at processing mathematical calculations. Hashing algorithms are simply a series of complex mathematical calculations. So it is better to GPU to crack the passwords.
Objectives
We are trying to use GPU to crack the passwords rather than CPU. We want to install John the Ripper and Hashcat(both are password crackers) in CUDA machine and use the GPUs in that machine to crack the passwords.
GPU
The graph shows the comparison between GPU and CPU
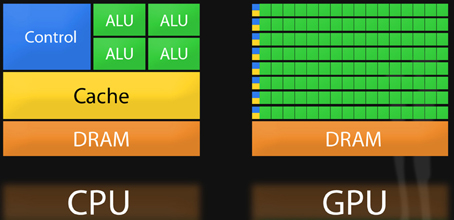
- Due to its design, the GPU is specialized for intensive, highly parallel computation
- A typical GPU consists of the same elements as a normal CPU
The graph shows what we used for experiments

- GPU: 1 Kepler GK 110B
- Memory Size: 12 GB
- Cores: 2880
Experiment
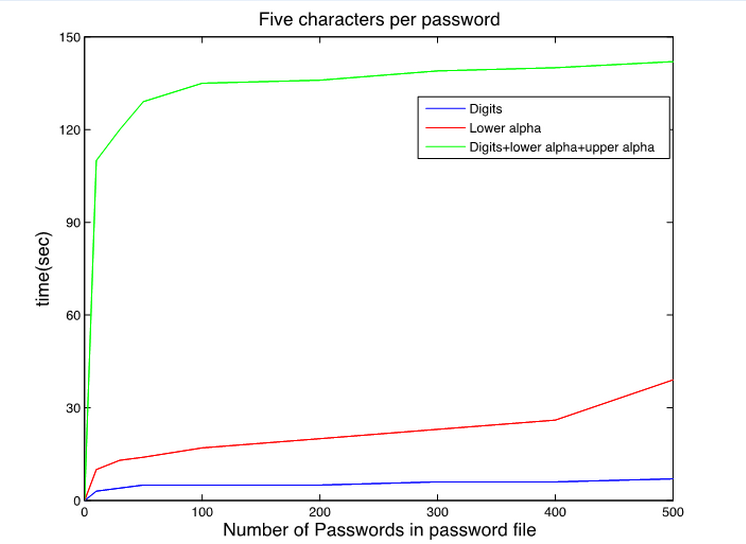
Initial trial were conducted using the CPU to see what kinds of passwords was the easiest to crack
- The password files consisted of random numbers, random letters, and a mix of random numbers and letters
- Used Brute Force Attack
- From the trial, the passwords of combination of numbers and letters are the most difficult type to crack
- The passwords only contain numbers are the most easiest type to crack
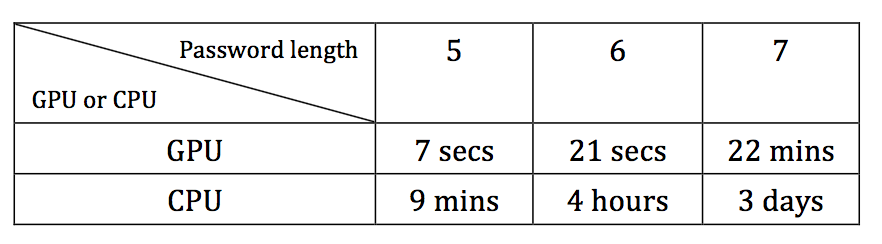
Trial was conducted using both the CPU and GPU to prove that the GPU was much faster
- Password files just contain numbers
- Password length varied from 5 to 7 and use Brute Force Attack
- The password length can dramatically influence cracking time
- GPU can increase the password cracking time significantly
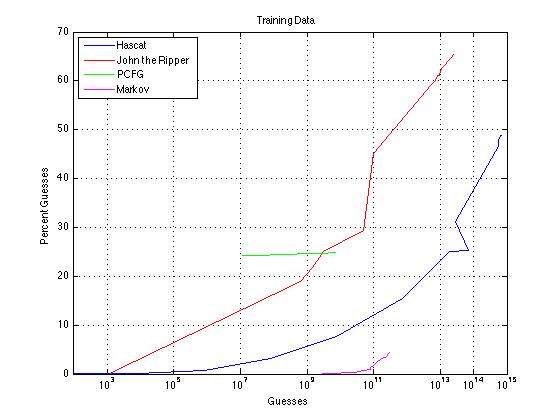
The next step was to see how many passwords can be cracked with an upper limit of 1015 guesses
- Used a leaked password list which contains 1,571,804 number of passwords
- Used John the Ripper, hashcat, PCGF and Markov model
- From the current trials, John the Ripper was able to crack the largest percentage of passwords
- The problem with John the Ripper is that it was a very long time to crack passwords, it was not able to reach 1015 guesses even though the trial ran 17 days
- Hashcat was a much shorter trial of only 5 days and it approached 1015 guesses
- PCFG was able to crack about 25% of the passwords with only 109 guesses which is more than both John the Ripper and Hashcat, but John the Ripper and Hascat kept increasing while PCFG was stagnant
- Markov model is the most inefficient one for password cracking
Tools and Resources
http://www.openwall.com/john/
http://hashcat.net/oclhashcat/
Attachments (5)
-
final graph.jpg
(32.8 KB
) - added by 11 years ago.
Final experiment graph
- comparsion.jpg (101.4 KB ) - added by 11 years ago.
- gpu.jpg (494.0 KB ) - added by 11 years ago.
- gpucpu.jpg (36.1 KB ) - added by 11 years ago.
- result1.jpg (69.6 KB ) - added by 11 years ago.
Download all attachments as: .zip